- 未分類

NFC/QR-Code/Face Recognition Payment Technology
A) NFC Payment Technology
Near Field Communication (NFC) technology is one of the core payment technologies in the Tips Payment and Receive System. It allows users to make secure payments within a very short distance via a smartphone or other NFC-compatible device.
- Fast response: NFC payments can be made almost instantly, greatly reducing payment waiting time.
- Convenient operation: Users only need to bring the device close to the payment terminal to complete the payment easily.
- High security: NFC payment uses advanced encryption technology to ensure the security of transaction data.
- Wide compatibility: It supports various smart devices to satisfy different users’ device usage.
B) QR-Code payment method
- Easy to use: Users only need to open the camera or dedicated application of the smartphone and scan the QR-Code of the payee to complete the payment quickly.
- Universal acceptance: QR-Code has become a globally accepted payment method that does not require specific hardware support.
- Flexible: Can be used in a variety of payment scenarios, both offline and online.
C) Face Recognition Payment System
Facial Recognition Payment System represents the latest trend in payment technology and plays an important role in the “Tips Payment and Receive System”.
- Advanced Security: Complex algorithms are used to recognize and validate the user’s facial features to ensure security.
- Touchless Payment: Users can make payments without touching any device.
- User Experience Optimization: Provides a fast and convenient payment experience to enhance user satisfaction.
- Cutting-edge technology: represents the cutting-edge development of payment technology and enhances the innovative image of the system.
2.2 Algorithm System Introduction
A) Design Philosophy
Cryptonight algorithm was originally designed to embody a deep understanding of cryptocurrency transactions and a focus on user needs.
- Hardware Friendly: Cryptonight aims to provide a cryptographic method that is friendly to common hardware devices. Users do not need high-end or specialized hardware to trade and mine cryptocurrencies efficiently.
- Anonymity and Security: The algorithm is designed with a focus on ensuring the anonymity and security of each transaction. This not only protects the user’s privacy, but also enhances the security of the entire payment network.
B) Algorithm Structure
- Complex Hash Functions: The algorithm uses a specially designed hash function to process the transaction data and generate unique hash values.
- Security of the hash values: These hash values are extremely secure as they are almost impossible to reverse engineer and decrypt. This makes it virtually impossible for an attacker to reproduce or tamper with the transaction data.
- Irreversibility of data: Once the transaction data is hashed, the original data can no longer be recovered or identified, thus ensuring the confidentiality and security of the transaction.
C) Algorithm Anonymity & Security
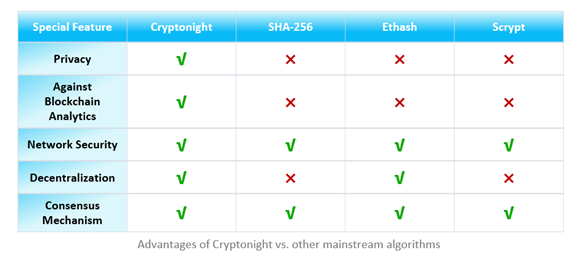
- Privacy Protection Mechanism: Ensuring the anonymity of user transactions through complex encryption technology, Cryptonight hides key information about the transaction, such as the addresses of the sender and receiver, and the amount of the transaction. The algorithm uses ring-signature technology, making it impossible for outside observers to trace the true origin of a transaction, thus protecting the privacy of the user’s transactions.
- Resistant to blockchain analytics: Transaction data is difficult to analyze and trace, even on public blockchains. This resistance to surveillance is especially useful for users and scenarios where privacy is important.
- Network Security: Due to the decentralized nature of the algorithms, there is no need to rely on a single trusted entity, thus increasing the overall security of the network. The consensus mechanism ensures that all participants in the network can agree on the validity of transactions, thus preventing potential network attacks.
2.3 Security mechanism against double-flower attack
A) About Double Spend Attack
A double-spend attack is a key security concern in digital currency transactions, where the same unit of digital currency is improperly reused multiple times. This behavior violates the basic principle of digital currency, which is that each unit of currency can only be consumed once.
B) Security mechanism design
- Transaction authentication mechanism: The system has built-in a strict transaction authentication process. Each transaction has to go through multiple validations before it is recognized by the network node, including signature verification, transaction input and output checks, etc. These validations ensure the legitimacy of the transaction. These verifications ensure the legitimacy and integrity of the transaction.
- Blockchain Technology Application: By utilizing blockchain technology, each transaction is recorded in an immutable public ledger. Once a transaction is added to the blockchain, it cannot be modified or deleted, which provides strong technical support to prevent double-spending.
- Network Monitoring and Consensus Algorithms: The system continuously monitors network activity in order to detect and respond to suspicious transactions in a timely manner. At the same time, consensus algorithms (e.g., proof of workload or proof of entitlement) are used to ensure that network nodes agree on transaction validation, further enhancing the ability to prevent double-spending.
2.4 System interfacing solution with cashier system
A) Interfacing Strategy
- Standardized interfaces: APIs follow industry standards to ensure compatibility with a wide range of different cashiering systems, including but not limited to POS systems, online payment platforms and mobile payment applications.
- Customized Adaptation: In addition to standard interfaces, we also provide customization services to meet the unique requirements of specific cashier systems, ensuring seamless integration with both traditional and modern payment systems.
- Security and Stability: The interface design emphasizes the security of data transmission and system stability, using advanced encryption technology and efficient data processing mechanisms.
B) Seamless Integration
- Intelligent Tipping Calculation: The system’s built-in intelligent algorithm can recommend the appropriate amount of tips based on the amount of consumption, user habits and other factors, which is not only convenient for consumers, but also improves the efficiency of service providers.
- Data Integration and Analysis: The integrated system collects and analyzes transaction data to provide merchants with valuable insights, such as consumer behavior analysis and revenue trend forecasts, to help them better understand the market and customer needs.
- Automated Billing: The cashiering system automatically recognizes transactions made through our payment system, enabling real-time billing and processing. This includes automatic calculation and display of tips, simplifying the billing process.